The default firewall configuration tool for Ubuntu is UFW (uncomplicated firewall). It was developed to ease iptables firewall configuration. By default UFW is disabled, and there are no packet filter rules in the Linux kernel:
# iptables -L -n --line-numbers Chain INPUT (policy ACCEPT) num target prot opt source destination Chain FORWARD (policy ACCEPT) num target prot opt source destination Chain OUTPUT (policy ACCEPT) num target prot opt source destination |
When you turn UFW on, it uses a default set of rules that should be fine for the average home user. In short, all incoming connections will be denied, thus protecting the system from intruders. To turn UFW on:
# ufw enable Firewall is active and enabled on system startup |
Once enabled, you are done! All future incoming connections will be denied. This configuration will be reloaded at boot.
You can easily view the status of ufw:
# ufw status Status: active |
If you are interested in seeing what UFW did, then run the following command to output the current UFW rules that are applied to your iptables. While it looks like UFW has done a lot, most of this is benign. UFW basically sets up a framework in order for it to easily add additional rules in the future, as well as faciliting logging.
# iptables -L -n --line-numbers Chain INPUT (policy DROP) num target prot opt source destination 1 ufw-before-logging-input all -- 0.0.0.0/0 0.0.0.0/0 2 ufw-before-input all -- 0.0.0.0/0 0.0.0.0/0 3 ufw-after-input all -- 0.0.0.0/0 0.0.0.0/0 4 ufw-after-logging-input all -- 0.0.0.0/0 0.0.0.0/0 5 ufw-reject-input all -- 0.0.0.0/0 0.0.0.0/0 6 ufw-track-input all -- 0.0.0.0/0 0.0.0.0/0 Chain FORWARD (policy DROP) num target prot opt source destination 1 ufw-before-logging-forward all -- 0.0.0.0/0 0.0.0.0/0 2 ufw-before-forward all -- 0.0.0.0/0 0.0.0.0/0 3 ufw-after-forward all -- 0.0.0.0/0 0.0.0.0/0 4 ufw-after-logging-forward all -- 0.0.0.0/0 0.0.0.0/0 5 ufw-reject-forward all -- 0.0.0.0/0 0.0.0.0/0 Chain OUTPUT (policy ACCEPT) num target prot opt source destination 1 ufw-before-logging-output all -- 0.0.0.0/0 0.0.0.0/0 2 ufw-before-output all -- 0.0.0.0/0 0.0.0.0/0 3 ufw-after-output all -- 0.0.0.0/0 0.0.0.0/0 4 ufw-after-logging-output all -- 0.0.0.0/0 0.0.0.0/0 5 ufw-reject-output all -- 0.0.0.0/0 0.0.0.0/0 6 ufw-track-output all -- 0.0.0.0/0 0.0.0.0/0 Chain ufw-after-forward (1 references) num target prot opt source destination Chain ufw-after-input (1 references) num target prot opt source destination 1 ufw-skip-to-policy-input udp -- 0.0.0.0/0 0.0.0.0/0 udp dpt:137 2 ufw-skip-to-policy-input udp -- 0.0.0.0/0 0.0.0.0/0 udp dpt:138 3 ufw-skip-to-policy-input tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:139 4 ufw-skip-to-policy-input tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:445 5 ufw-skip-to-policy-input udp -- 0.0.0.0/0 0.0.0.0/0 udp dpt:67 6 ufw-skip-to-policy-input udp -- 0.0.0.0/0 0.0.0.0/0 udp dpt:68 7 ufw-skip-to-policy-input all -- 0.0.0.0/0 0.0.0.0/0 ADDRTYPE match dst-type BROADCAST Chain ufw-after-logging-forward (1 references) num target prot opt source destination 1 LOG all -- 0.0.0.0/0 0.0.0.0/0 limit: avg 3/min burst 10 LOG flags 0 level 4 prefix "[UFW BLOCK] " Chain ufw-after-logging-input (1 references) num target prot opt source destination 1 LOG all -- 0.0.0.0/0 0.0.0.0/0 limit: avg 3/min burst 10 LOG flags 0 level 4 prefix "[UFW BLOCK] " Chain ufw-after-logging-output (1 references) num target prot opt source destination Chain ufw-after-output (1 references) num target prot opt source destination Chain ufw-before-forward (1 references) num target prot opt source destination 1 ufw-user-forward all -- 0.0.0.0/0 0.0.0.0/0 Chain ufw-before-input (1 references) num target prot opt source destination 1 ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 2 ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED 3 ufw-logging-deny all -- 0.0.0.0/0 0.0.0.0/0 state INVALID 4 DROP all -- 0.0.0.0/0 0.0.0.0/0 state INVALID 5 ACCEPT icmp -- 0.0.0.0/0 0.0.0.0/0 icmptype 3 6 ACCEPT icmp -- 0.0.0.0/0 0.0.0.0/0 icmptype 4 7 ACCEPT icmp -- 0.0.0.0/0 0.0.0.0/0 icmptype 11 8 ACCEPT icmp -- 0.0.0.0/0 0.0.0.0/0 icmptype 12 9 ACCEPT icmp -- 0.0.0.0/0 0.0.0.0/0 icmptype 8 10 ACCEPT udp -- 0.0.0.0/0 0.0.0.0/0 udp spt:67 dpt:68 11 ufw-not-local all -- 0.0.0.0/0 0.0.0.0/0 12 ACCEPT udp -- 0.0.0.0/0 224.0.0.251 udp dpt:5353 13 ACCEPT udp -- 0.0.0.0/0 239.255.255.250 udp dpt:1900 14 ufw-user-input all -- 0.0.0.0/0 0.0.0.0/0 Chain ufw-before-logging-forward (1 references) num target prot opt source destination Chain ufw-before-logging-input (1 references) num target prot opt source destination Chain ufw-before-logging-output (1 references) num target prot opt source destination Chain ufw-before-output (1 references) num target prot opt source destination 1 ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 2 ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED 3 ufw-user-output all -- 0.0.0.0/0 0.0.0.0/0 Chain ufw-logging-allow (0 references) num target prot opt source destination 1 LOG all -- 0.0.0.0/0 0.0.0.0/0 limit: avg 3/min burst 10 LOG flags 0 level 4 prefix "[UFW ALLOW] " Chain ufw-logging-deny (2 references) num target prot opt source destination 1 RETURN all -- 0.0.0.0/0 0.0.0.0/0 state INVALID limit: avg 3/min burst 10 2 LOG all -- 0.0.0.0/0 0.0.0.0/0 limit: avg 3/min burst 10 LOG flags 0 level 4 prefix "[UFW BLOCK] " Chain ufw-not-local (1 references) num target prot opt source destination 1 RETURN all -- 0.0.0.0/0 0.0.0.0/0 ADDRTYPE match dst-type LOCAL 2 RETURN all -- 0.0.0.0/0 0.0.0.0/0 ADDRTYPE match dst-type MULTICAST 3 RETURN all -- 0.0.0.0/0 0.0.0.0/0 ADDRTYPE match dst-type BROADCAST 4 ufw-logging-deny all -- 0.0.0.0/0 0.0.0.0/0 limit: avg 3/min burst 10 5 DROP all -- 0.0.0.0/0 0.0.0.0/0 Chain ufw-reject-forward (1 references) num target prot opt source destination Chain ufw-reject-input (1 references) num target prot opt source destination Chain ufw-reject-output (1 references) num target prot opt source destination Chain ufw-skip-to-policy-forward (0 references) num target prot opt source destination 1 DROP all -- 0.0.0.0/0 0.0.0.0/0 Chain ufw-skip-to-policy-input (7 references) num target prot opt source destination 1 DROP all -- 0.0.0.0/0 0.0.0.0/0 Chain ufw-skip-to-policy-output (0 references) num target prot opt source destination 1 ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 Chain ufw-track-input (1 references) num target prot opt source destination Chain ufw-track-output (1 references) num target prot opt source destination 1 ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW 2 ACCEPT udp -- 0.0.0.0/0 0.0.0.0/0 state NEW Chain ufw-user-forward (1 references) num target prot opt source destination Chain ufw-user-input (1 references) num target prot opt source destination Chain ufw-user-limit (0 references) num target prot opt source destination 1 LOG all -- 0.0.0.0/0 0.0.0.0/0 limit: avg 3/min burst 5 LOG flags 0 level 4 prefix "[UFW LIMIT BLOCK] " 2 REJECT all -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-port-unreachable Chain ufw-user-limit-accept (0 references) num target prot opt source destination 1 ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 Chain ufw-user-logging-forward (0 references) num target prot opt source destination Chain ufw-user-logging-input (0 references) num target prot opt source destination Chain ufw-user-logging-output (0 references) num target prot opt source destination Chain ufw-user-output (1 references) num target prot opt source destination |
This is the rule in the INPUT chain above that drops incoming connections:
DROP all -- 0.0.0.0/0 0.0.0.0/0 |
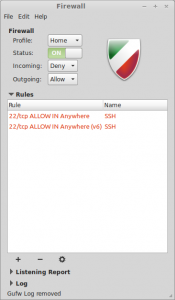
You may want to install gufw. It is a graphical user interface for UFW that provides an easy and intuitive way to manage your Linux firewall. It supports common tasks such as allowing or blocking ports. There is a status switch that can be turned on and off, which basically performs the commands “ufw enable” and “ufw disable“.
My System Configuration
- Linux Mint 16 Petra x86 64-bit